Mixed Criticality Systems Enabled on ARMv8 Architectures To Power Automotive IVI Gateways

An important trend in the design of embedded systems is the integration of applications with different levels of criticality to interact and co-exist on a common hardware platform. Most of the complex embedded systems found in, for example, the automotive industry are evolving into mixed criticality systems in order to meet requirements relating to cost, space, weight, power and consumption. For example, a connected car contains the safety-critical drive systems (e.g., Break, electric-assist steering, etc.) that have to be isolated from the passenger entertainment system (IVI). The main challenges to address in mixed criticality systems includes real-time behavior, memory isolation, data and control coupling.
To solve this challenging equation, Virtual Open Systems proposes a solution based on ARM TrustZone, which allows to run concurrently a trusted RTOS (Real-Time Operating System) in the secure world for critical operations and a GPOS (General-Purpose Operating System) with virtualization in the normal world. TrustZone defines a secure operational mode than can be completely isolated (memory, devices and so on) from the normal mode. Moreover the implementation is defined to give the full priority to the secure world application in order to meet the real-time constraints.
To achieve a first , such as JUNO ARM Development Platform, a software solution development has been started with ARM Trusted Firmware (ATF). ATF is an ARMv8 open source framework to use Trustzone and boots a Secure payload and a Non trusted firmware (e.g., U-Boot, etc.) in the Secure world and the Normal world respectively. The context switch between Secure and Normal world is only possible in an exception layer called Secure monitor or EL3. Virtual Open Systems has extended the ATF BL31 layer which contains the EL3 firmware.
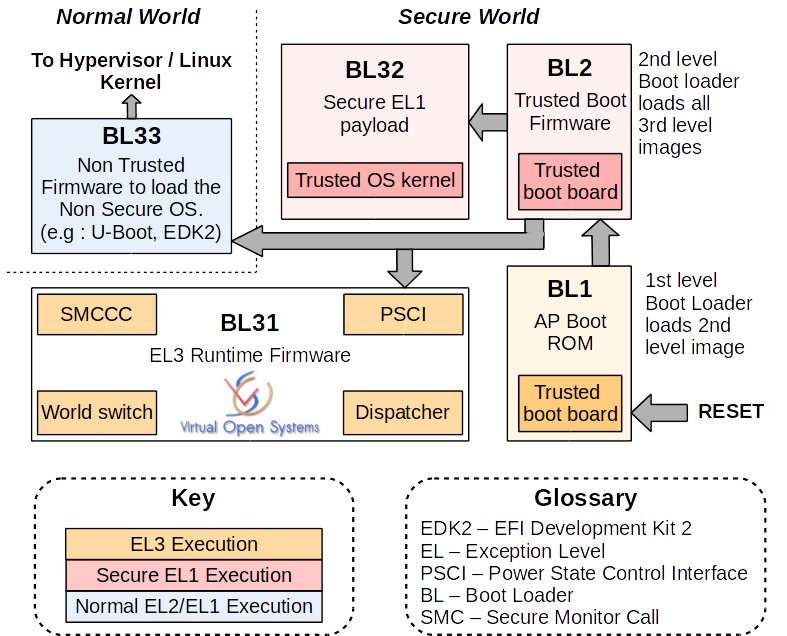
Virtual Open Systems extensions in ARM trusted firmware layer, modified from http://community.arm.com/docs/DOC-9306
The extended functionalities developed by Virtual Open Systems in this EL3 firmware consist to:
- Change secure interrupt management for routing in EL3 layer
- Add services in EL3 to execute a legacy RTOS in the Secure world
- Optimize context switch for a 32-bit Secure payload
Virtual Open Systems functionality mixed-criticality extensions in ARM Trusted Firmware
FIQ handling in the monitor
Virtual Open Systems has extended the ATF code base to trap all secure interrupts in the Secure monitor. Indeed, with the available ATF implementation and since Virtual Open Systems architecture gives the full priority to the RTOS, the Secure monitor doesn't have any means to recover control if RTOS monopolizes the execution context (e.g., Trusted OS crash, infinity loop, etc.). The Virtual Open Systems' proposal extends the Secure Monitor functionality to recover from such cases.
enable the handling of secure interrupts only in EL3, where the monitor could take decisions based on interrupt ID, about the interrupt destination, either monitor or RTOS. The decision making is not part of this contribution and is left open to the specific needs of the target platform. Current work assumes that all secure interrupts are redirecting to RTOS. To enable handling in EL3, ARM Trusted Firmware has to be build with TSPD_ROUTE_FIQ_TO_EL3=1.
ATF works seamlessly with or without TSPD_ROUTE_FIQ_TO_EL3 enabled. The main change related to this implementation is to improve the system robustness by allowing the Secure monitor to execute an action when a specific secure interrupt occurs. However, such a software solution is not optimal in the sense that it increases the interrupt handling latency when the secure interrupts fire during the Secure world execution. Indeed such interrupts, in generic ATF, are directly handled in RTOS. This overhead boils down to:
- Saving operations
- Secure monitor management
- Restore operations
The ATF with the FIQ-EL3 handling functionality can be downloaded from:
git clone https://github.com/virtualopensystems-kchappuis/arm-trusted-firmware.git -b fiq_el3_INTR_TYPE_S_EL1
The port of FreeRTOS v8.2.2 is available at the forum of FreeRTOS Community Contributions
To overcome the interrupt latency limitation brought with this implementation, Virtual Open Systems has developed its own Secure Monitor Firmware, called VOSYSmonitor, which runs concurrently a RTOS in the Secure world for critical operations as well as a virtualized General Purpose OS (GPOS) in the Normal world. The VOSYSmonitor targets to forward an interrupt to the Secure world in less than 1 microsecond, whereas the Normal world is running.
Service dispatcher to support Trusted 32-bit OS
Virtual Open Systems has extended the ATF code base to support the execution of a 32-bit OS in the Secure world. Indeed, with the current ATF implementation, the Secure monitor can only execute a Trusted 64-bit 0S. With its ATF extension, Virtual Open Systems adds a new dispatcher in the ATF to support a Trusted kernel 32-bit. To enable it, ARM Trusted Firmware has to be build with TSP_AARCH32_MODE=1 and SPD=tspd_aarch32.
To test this new functionality, Virtual Open Systems has ported the FreeRTOS v8.2.2, which is one of the most popular 32-bit real time operating system for embedded systems, on two ARM platforms (e.g., ARM Juno Development Board and ARM Fast Models), in order to run it as a Trusted 32-bit OS with ARM Trusted Firmware.
The ATF with the Dispatcher code for Trusted 32-bit OS can be downloaded from:
git clone https://github.com/virtualopensystems-kchappuis/arm-trusted-firmware.git -b tspd_aarch32_service
FreeRTOS v8.2.2 port is available in the FreeRTOS Community Contributions website:
http://interactive.freertos.org/entries/83649935-FreeRTOS-v8-2-2-port-AARCH32-for-ARMv8-platform-ARM-FastModel-virtual-platform-and-ARM-JUNO-Developm
Custom services for firmware development on ARM architecture
Thanks to its experience on virtualization and low level software programming of heterogeneous systems (e.g., KVM, ARMv7 and ARMv8 based SoCs), Virtual Open Systems is an experienced development partner for the implementation of professional custom development services aiming to support firmware applications for ARM platforms in embedded mixed-critical systems:
- ARMv7-A and ARMv8-A architectures
- Firmware application development (Assembly ARM, Assembly GCC, C)
- Exception management (FIQ, IRQ, SMC...)
- Secure Monitor, Hypervisor
- Generic Interrupt Controller v2/v3
- Memory Management Unit
- KVM virtualization
 VOSySofficial
VOSySofficial