Cloud & Edge Trusted Virtualized Infrastructure Manager (VIM) - Security and Trust in OpenStack

The Cloud & Edge Trusted VIM software product (VOSyStrustedvim) developed by Virtual Open Systems is meant to add security and trust into virtualized infrastructures. Based on OpenStack, it protects the computing environment, provides crypto features to the virtual machines, facilitates the control of workloads placement and regulates it. Use cases for this technology are all the cloud and edge virtualized infrastructure, e.g., smart cities, healthcare, smart roads, public safety, financial services, manufacturing, energy, media and entertainment.
The security challenge in edge devices
Security and trust are essential in edge computing environments because of the increasing sensitive data they process and their distributed architecture. Especially with edge devices, the risk of man-in-the-middle and denial of service attacks is significant. To make things worse, they are often placed in positions difficult to secure making relatively easy for an attacker to physically modify, replace or tamper them. A device with a fake identity or one infected with malicious software can compromise the entire computing infrastructure.
The solution provided by VOSyStrustedvim
In response to these challenges, the Cloud & Edge Trusted VIM (VOSyStrustedvim) enhances security, attests devices and protects sensitive data. For instance, before each virtual machine placement, the compute nodes are authenticated and the host operating system integrity is verified by VOSyS Trusted Open Stack Extensions. Moreover, the hypervisor and virtual machines are enhanced with the cryptographic and security functions of a vTPM (virtual Trusted Platform Module). In addition, VOSyS Secure Services are isolated from potential attackers by running in a Trusted Execution Environment built upon VOSYSmonitor, a highly privileged software that ensures an isolation at the hardware level by leveraging ARM TrustZone technology.
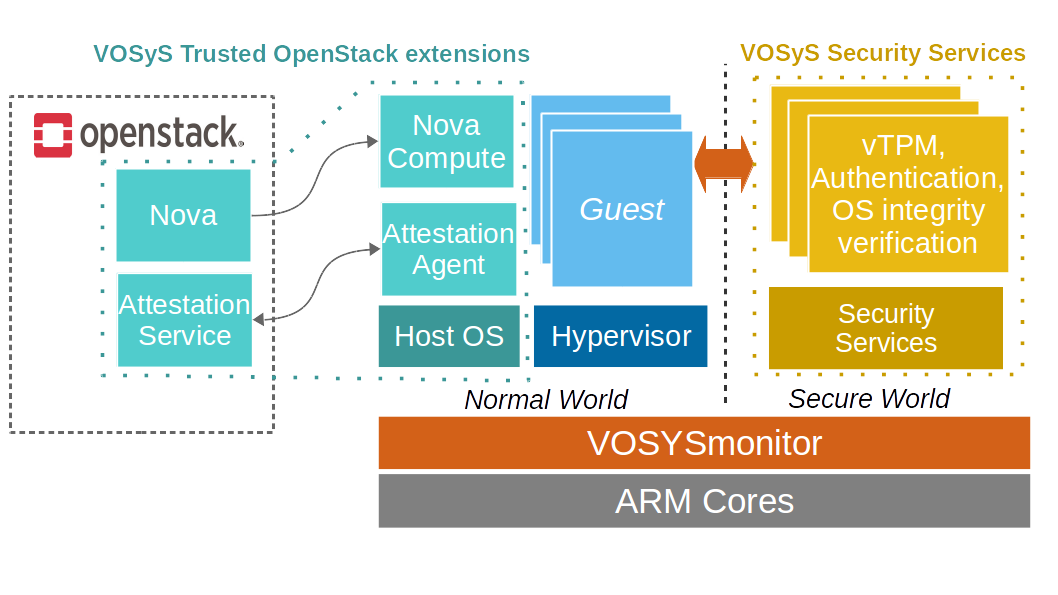
Cloud & Edge Trusted VIM overview
Main Features & Benefits
VOSyStrustedvim implements a set of trust operations to ensure the security of edge devices:
- Remote host authentication: OpenStack compute nodes are being authenticated before VMs can be run on them, this way avoiding man-in-the-middle or device replacement attacks.
- Host operating system integrity verification: the operating system kernel is checked for unknown modifications, detecting untrusted activities (malicious software, rootkits, etc.).
- Trusted Boot: ensures the trustworthiness of the system is propagated throughout all software layers.
- vTPM: virtual Trusted Platform Module provides each VM with enhanced security and cryptographic capabilities.
- Geo-tagging: helps apply regulatory policies by constraining workloads and data to certain geographic regions.
Virtual Open Systems Contact
For any inquiry related to VOSyStrustedvim product and custom product extension services, you can contact us.
- Kvm performance
- Virtual bfq
- Vosyshmem zerocopy
- Vosysmonitor
- Api remoting
- Vosyswitch nfv virtual switch
- Accelerators virtualization interface
- Vosysmonitor jp 日本語
- Vosysmonitorx86 jp 日本語
- Vosysiot edge
- Vfpgamanager
- Vosysvirtualnet
- Vosysmcs
- Vosysmonitor sossl framework
- Vosysmonitorx86
- Vosysmonitorv risc v
- Vosysmonitorv risc v jp 日本語
- vosysvirtualnet jp 日本語
- Vosyszator
- Vmanager
 VOSySofficial
VOSySofficial