VOSYSmonitor, a Low Latency Certified Monitor Layer for Mixed-Criticality Systems on ARM architecture

In mixed critical systems, a key design requirement is the consolidation of software applications with different levels of criticality on a common hardware platform. For instance in avionics, functions are usually classified either as flight-critical (necessary for ensuring a safe flight) or mission-critical (essential for business execution). Likewise in automotive domain, the traditional practice used to isolate safety critical applications is through proliferation of many hardware Engine Control Units (ECUs), which are dedicated to basic operations, such as Body Control Module (e.g., monitors and control power windows, power mirrors, air conditioning, central locking, etc), to critical tasks as Electronic Braking System (EBS), engine control and digital instrument cluster.
This is a highly inefficient way of using the available processing power since many of these hardware units are typically not used at their full potential. However, recent multi-core SoC architectures with new hardware extensions (e.g., virtualization, TrustZone) as well as the high demand for rich features, tend to combine mixed-criticality systems on the same platform, thus reducing costs and helping to increase efficiency. The consolidation of different Operating Systems (OSes) on the same platform implies the concurrent execution of a critical OS with stringent real-time and safety requirements along with non-critical applications. In this context, a major challenge is the execution of real-time tasks and software applications running on a General Purpose OS (GPOS) within highly isolated virtual machines.
VOSYSmonitor enables RTOS & virtualized GPOS in mixed-critical systems
With this challenging target in mind, Virtual Open Systems offers VOSYSmonitor, a powerful product solution, which consists in a low level certified software layer developed on the ARM architecture. VOSYSmonitor allows to co-execute on the same hardware platform both a safety critical Real Time Operating System (RTOS) and a plurality of General Purpose Operating System (GPOS), by using virtualization technologies.
This software layer isolates the RTOS from the virtualized instances and provides, at the same time, functions to enable a safe and secure communication between them. VOSYSmonitor is based on ARM TrustZone technology, which enforces among others, memory, CPU and interrupt isolation between the RTOS and the GPOS. The design goal of VOSYSmonitor is to give the full priority to the secure world application in order to meet real-time constraints, while being compliant with safety standards (ISO 26262, IEC 61508, EN 50128). Last but not least, known vulnerabilities are always considered and controlled. As a matter of fact, VOSYSmonitor has been enhanced to be resilient against the Spectre/Meltdown vulnerabilities.
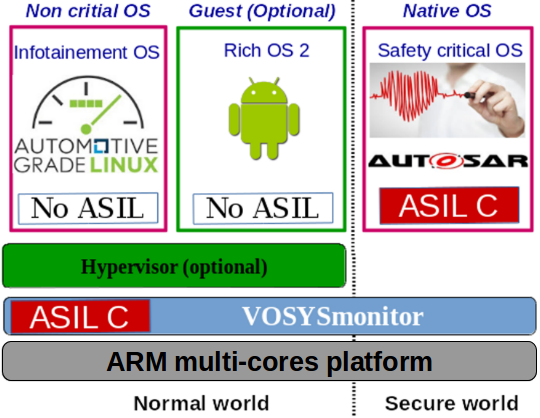
VOSYSmonitor system overview
In mixed-criticality domains, functional safety has become a key and strong requirement. Functional safety generally ensures that malfunctions of the operating system, which contain mission-critical tasks that lead to any kind of threat or even severe accident, have to be avoided or mitigated. Several safety standards exists, such as the IEC 61508 - Electrical/Electronic/Programmable Electronic Safety-related Systems, which can be used on any industry related product.
A more specific safety standard, the ISO 26262 – Road vehicles – Functional Safety has been created for the automotive system in order to define a functional safety lifecycle for each automotive product development phase, ranging from the hazard analysis and risk assessment to design, implementation, integration, verification, validation and production release.
Since VOSYSmonitor aims to consolidate safety critical applications, it is required to be certifiable with the same Safety Integrity Level (SIL for IEC 61508, ASIL for ISO 26262) than the critical system running on top of it. In this context, Virtual Open Systems applies a strict V-Cycle compliant with the ISO 26262 standard for the development of VOSYSmonitor in order to identify the potential hazards and safety requirements as well as to specify, implement and test the corresponding countermeasures that aim to prevent/mitigate failures.
In cases where VOSYSmonitor is used in other domains than the automotive, the applying certification process is facilitated as the product is already certified for ISO 26262. For instance, for a medical use-case requiring an IEC 60601 certification or a railway use-case requiring an EN 50128 certification, a gap analysis can be performed by a certification company, thus avoiding a certification process from scratch.
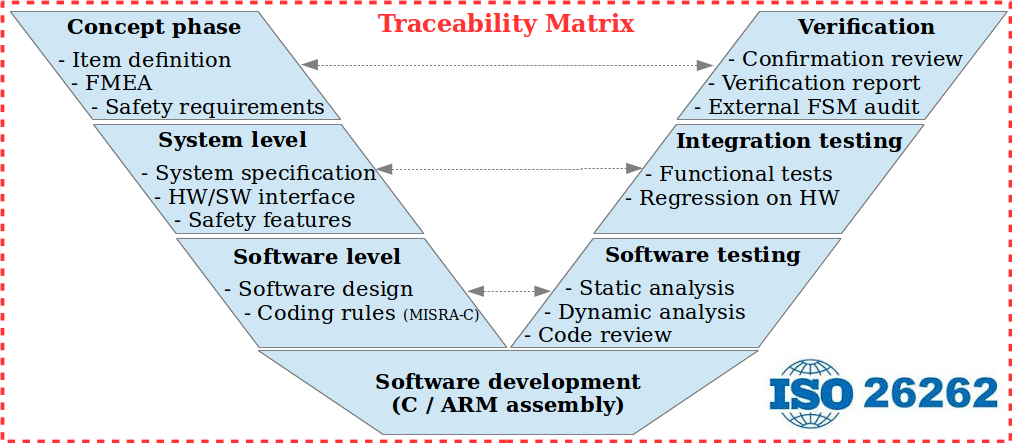
VOSYSmonitor in automotive - V-Cycle ISO 26262 Road vehicles Functional Safety
VOSYSmonitor is meant to be the key component of VOSySmcs, an automotive mixed-criticality virtualization software stack, which integrates open source components (including certified RTOS). Through its open and scalable virtualization architecture, VOSYSmcs opens, unlike competitive closed solution, to support a completely new generation of software driven vehicles, where autonomous driving and their virtualized access to AI hardware acceleration mechanism can be orchestrated and executed in isolated virtual machines, with stringent ISO-26262 certification requirements. Moreover, outcomes from standards and initiatives such as IVI automotive AGL software stack, GENIVI, Autosar, ADAS are monitored and continuously integrated into the VOSySmcs to provide customers with latest updates from these communities.
VOSYSmonitor is also part of VOSYSIoT, a virtualization software stack product, which enables the processing of highly sensitive and time-critical data along with non-critical data on a single IoT edge platform. Such an architecture allows to design safety-aware IoT gateways and edge nodes with special attention to safety and security, while reducing the overall cost (e.g., space, power consumption, materials, integration effort).
VOSYSmonitor, monitor layer main features
VOSYSmonitor has been designed to be compliant with the stringent ISO -26262 certification. It's based on a scalable and modular architecture, as shown hereafter:
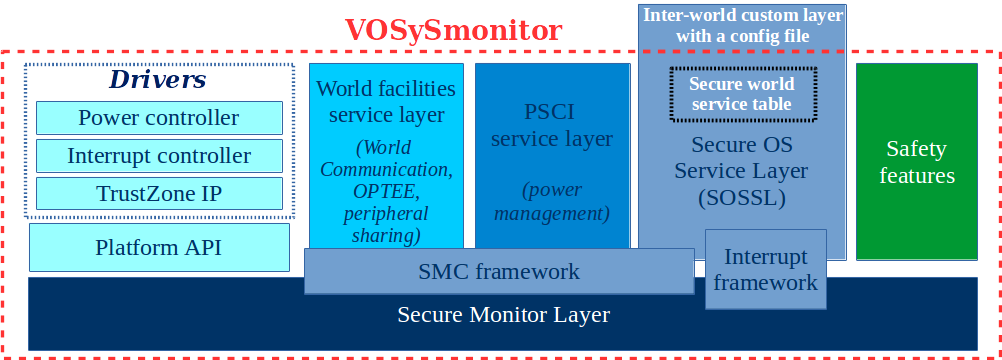
VOSYSmonitor software architecture
- SOSSL: Interface between the Secure OS and the monitor layer to dispatch SMC services as well as to handle interrupts forwarding.
- PSCI: Service layer for power management services (Power ON/OFF cores, etc).
- World facilities Service Layer: VOSYSmonitor custom services (e.g., inter-world communication channel) in order to provide advanced features to systems running in each world.
- EL3 Monitor Layer: Specifically implemented for ARM architecture, it handles the world context switch operations triggered by SMC instruction or hardware exception mechanisms.
- Platform API: Functions to abstract Drivers function calls from EL3 Monitor Layer.
- Safety features: Countermeasures (e.g., safe state, self-tests, etc) to preserve the Secure OS in case of internal / hardware failures.
VOSYSmonitor supports ARMv7 as well as the last generations of ARMv8 platforms, including the following:
- ARMv8 - Mediatek Autus I20 (MT2712) (2 Cortex-A72 + 4 Cortex A-35)
- ARMv8 - Renesas R-Car H3 board (4 Cortex-A57 + 4 Cortex A-53) – ISO-26262 compliant
- ARMv8 - Renesas R-Car M3 board (2 Cortex-A57 + 4 Cortex A-53) – ISO-26262 compliant
- ARMv8 - Xilinx Zynq UltraScale+ MPSoC (4 Cortex A-53)
- ARMv7 - Renesas RZ/N1D (2 Cortex A7)
- ARMv7 - Altera Cyclone V (2 Cortex A9)
- ARMv8 - ARM Juno Development board (r0 and r1: 2 Cortex-A57 + 4 Cortex A-53 / r2: 2 Cortex-A72 + 4 Cortex A-53)
- ARMv8 - NVIDIA Jetson TX1 board (4 x Cortex-A57/A53 in big.LITTLE configuration)
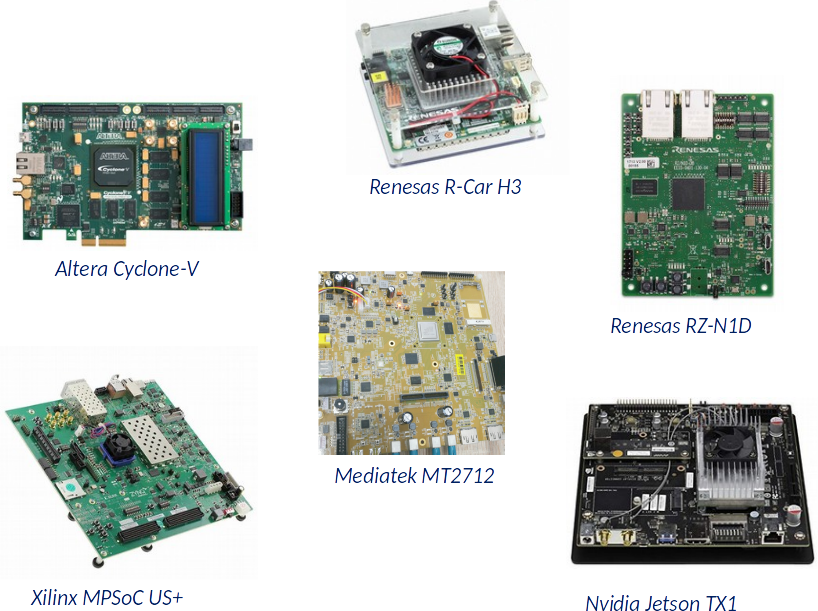
Hardware platforms supported by VOSySmonitor
Note
Virtual Open Systems is continuously supporting new platforms; if your platform is not listed here, contact us for more information.
The main features of VOSYSmonitor, which enables the co-execution of RTOS and virtualized GPOS, consist of:
- Mixed-criticality system consolidation on a single hardware platform
- Safety critical OS strong isolation using ARM TrustZone
- Fast context switch to meet real-time constraints
- Provide virtualization features for the GPOS
- Monitor the system to recover failures
- Scalable architecture
- Minimal changes to the GPOS and safety critical OS
Compared to traditional alternatives, VOSYSmonitor provides multiple key advantages:
- Strong isolation based on ARM TrustZone, VOSYSmonitor partitions system resources preventing unauthorized access to the safety critical environment (No IOMMU required).
- Modular and open architecture that does not impose any OS, tool, hypervisor, ROTS to mix the critical and non critical worlds.
- Reduced costs by proposing a bottom up solution, focusing on isolation, safety and performances of critical resources; pay only for what your use case requires.
Virtual Open Systems Contact
For any inquiry related to VOSYSmonitor product and custom porting services you can contact us.
- Kvm performance
- Virtual bfq
- Vosyshmem zerocopy
- Api remoting
- Vosyswitch nfv virtual switch
- Accelerators virtualization interface
- Vosysmonitor jp 日本語
- Vosysmonitorx86 jp 日本語
- Vosysiot edge
- Vfpgamanager
- Vosysvirtualnet
- Vosysmcs
- Vosystrustedvim
- Vosysmonitor sossl framework
- Vosysmonitorx86
- Vosysmonitorv risc v
- Vosysmonitorv risc v jp 日本語
- vosysvirtualnet jp 日本語
- Vosyszator
- Vmanager
 VOSySofficial
VOSySofficial